Data independence in DBMS
Data independence is the ability to change the schema at one level of the database system without having to change the schema at the other levels. Data independence is of two types, namely, logical data independence and physical data independence.
Logical data independence:
It is the ability to change the conceptual schema without affecting the external schemas or application programs. The conceptual schema may be changed due to change in constraints or addition of new data items or removal of existing data items, etc. from the database. The separation of the external level from the conceptual level enables the users to make changes at the conceptual level without affecting the external level or the application programs.
Physical data independence:
It is the ability to change the internal schema without affecting the conceptual or external schema. An internal schema may be changed due to several reasons such as for creating additional access structure, changing the storage structure, etc. The separation of internal schema from the conceptual schema facilitates physical data independence.
Logical data independence is more difficult to achieve than the physical data independence because the application programs are always dependent on the logical structure of the database.
Importance: Data independence is an important characteristic of DBMS as it allows changing the structure of the database without making any changes in the application programs that use the database.
Types of database users in DBMS
Database users are those who interact with the database in order to query and update the database and generate reports. Database users are classified into the following categories:
Naïve users: The users who query and update the database by invoking some already written application programs. For example, the owner of the bookstore enters the details of various books in the database by invoking an appropriate application program.
Sophisticated users: The users, such as a business analyst, scientist, etc., who are familiar with the facilities provided by a DBMS interact with the system without writing any application programs. Such users use database query language to retrieve information from the database to meet their complicated requirements.
Specialized users: The users who write specialized database programs that are different from traditional data-processing applications such as banking and payroll management use simple data types. Specialized users write applications such as computer-aided design systems, knowledge-base and expert systems that store data having complex data types.
Who is a database administrator (DBA)?
A database administrator (DBA) is a person who has central control over both data and application programs.
What are the various responsibilities of a DBA?
Some of the responsibilities of DBA are as follows:
Schema definition and modification: The overall structure of the database is known as the database schema. It is the responsibility of the DBA to create the database schema by executing a set of data definition statements in DDL.
New software installation: It is the responsibility of the DBA to install new DBMS software, application software and other related software. After installation, the DBA must test the new software.
Security enforcement and administration: DBA is responsible for establishing and monitoring the security of the database system. It involves adding and removing users, auditing and checking for security problems.
Data analysis: DBA is responsible for analyzing the data stored in the database and studying its performance and efficiency in order to effectively use indexes, parallel query execution, etc.
Preliminary database design: The DBA works along with the development team during the database-design stage due to which many potential problems that can arise later can be avoided.
Physical organization modification: The DBA is responsible for carrying out the modifications in the physical organization of the database for better performance.
Routine maintenance checks: The DBA is responsible for taking the database backup periodically in order to be able to recover from any hardware or software failure and restore the database to a consistent state.
Reasons for the need of a database
Following are some reasons for the need of a database:
- Database is required for efficient and easy storage, retrieval, updation and deletion of data records.
- Once a database is created, it can be shared by many users. Hence, to share data with many applications a database is required.
- Interrelated data should be grouped in one named storage area for easy access. This storage area may be physical or logical which resides in computer.
- For avoiding unnecessary repetition of data values, checking correctness of data by applying some validation rule, and searching the required information faster thus saving time and effort, etc.
- Database is required for flexibility, i.e., as and when required we can connect the database with different front-ends.
- Database is needed for storing high volume and complex data, such as documents files, photographs or images, multimedia data, mobile user’s data, audio and video files.
- For managing multi-dimensional data.
- Database is required for proper transaction management or transaction handling.
Architecture of DBMS
The DBMS architecture describes how data in the database are viewed by the users. It is not concerned with how the data are handled and processed by the DBMS. In this architecture, the overall database description can be defined at three levels namely, internal, conceptual and external levels and, thus, named three-level DBMS architecture (Figure below). The three levels are as follows:
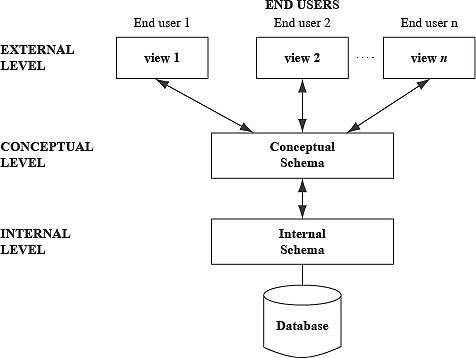
Internal level:
It is the lowest level of data abstraction that deals with the physical representation of the database on the computer and, thus, is also known as the physical level. It describes how the data are physically stored and organized on the storage medium.
Conceptual level:
This level of abstraction deals with the logical structure of the entire database and, thus, is also known as the logical level. It describes what data are stored in the database, the relationships among the data and a complete view of the user's requirements without any concern for the physical implementation.
External level:
It is the highest level of abstraction that deals with the user's view of the database and, thus, is also known as the view level. It permits users to access data in a way that is customized according to their needs, so that the same data can be seen by different users in different ways, at the same time. In this way, it provides a powerful and flexible security mechanism by hiding the parts of the database from certain users as the user is not aware of the existence of any attributes that are missing from the view.
These three levels are used to describe the schema of the database at various levels. Thus, the three-level architecture is also known as three-schema architecture.
Advantage of three-schema architecture
The main advantage of three-schema architecture is that it provides data independence. Data independence is the ability to change the schema at one level of the database system without having to change the schema at the other levels. The database users are provided with an abstract view of the data by hiding certain details of how data are physically stored. This enables the users to manipulate the data without worrying about where they are located or how they are actually stored.
Mapping in three-schema architecture.
In three-schema architecture, each user group refers only to its own external view. Whenever a user specifies a request to generate a new external view, the DBMS must transform the request specified at the external level into a request at the conceptual level, and then into a request at the physical level. If the user requests for data retrieval, the data extracted from the database must be presented according to the need of the user. This process of transforming the requests and results between various levels of DBMS architecture is known as mapping.
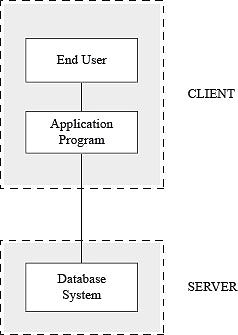
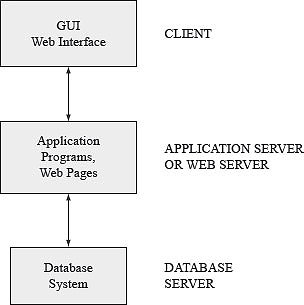
Two-tier architecture in DBMS
There are two approaches to implement client/server architecture. In the first approach, the user interface and application programs are placed on the client side and the database system on the server side. This architecture is called two-tier architecture. The application programs that reside at the client side invoke the DBMS at the server side. The application program interface standards like Open Database Connectivity (ODBC) and Java Database Connectivity (JDBC) are used for interaction between the client and the server. Figure below shows two-tier architecture.

The second approach is the three-tier architecture
Three-tier architecture
Other than two-tier architecture approach there is another approach available that is three-tier architecture, which is used for Web-based applications. It adds an intermediate layer known as the application server (or Web server) between the client and the database server. The client communicates with the application server, which in turn communicates with the database server. The application server stores the business rules (procedures and constraints) used for accessing data from the database server. It checks the client's credentials before forwarding a request to the database server. When a client requests for information, the application server accepts the request, processes it and sends corresponding database commands to the database server. The database server sends the result back to the application server, which is converted into GUI format and presented to the client. Figure below shows the three-tier architecture.


No comments:
Post a Comment